SSH key-based authentication
While the most common way of login to the HPCC is by using the username/password pair, a more secure authentication method is the use of SSH keys. Although setting up your keys is a little more complex, it is a one-time investment. The HPCC provides key-based authentication as an option, in addition to the usual password-based login.
Note
Starting in October 2022, login to our rsync gateway (rsync.hpcc.msu.edu) will accept SSH keys as the ONLY authentication method. Username/password won't work.
What are SSH keypairs?
An SSH keypair consists of a private key and a public key. Your private key is a secret key just like your password which you should not share with anyone. On the other hand, your public key can be made publicly available in the same way that your name can be made public. The public key is stored on the server you attempt to log into (that is, the HPCC), while the private key is stored on your own computer. When a user attempts to log in, an encryption process starts on the HPCC side, using the public key. With your private key, your computer will be able to decrypt the encrypted message sent from the HPCC. When everything matches up, your login is approved.
Via command line tools (Linux, MacOS, MobaXterm terminal on Windows)
SSH tool suites usually provide a utility for generating these keypairs. On a Mac and Linux, you can run the command ssh-keygen using the built in terminal Terminal.
On a Windows computer, you will first need to download MobaXterm to generate SSH key pairs. See the Intro to MobaXterm for more on getting started. Once you have installed MobaXerm, run the program and choose the "Start local terminal" option.
Generating SSH keypairs on command line
To generate a keypair from command line (e.g., after opening a terminal on Mac, Linux or through MobaXterm on Windows), run
ssh-keygen -t rsa -b 4096
You will be given an option for protecting your private key with a passphrase. Please do this, as it will prevent your private key from being used by a malicious individual if it is ever stolen.
After you have set a passphrase and the keys has generated, you will find the key's files in the .ssh directory under your home directory. By default, id_rsa is the private key file and id_rsa.pub the public key file.
Uploading your public key to the HPCC
In order to login to HPCC with key-based authentication from your local computer, you will need to add your public key to the ~/.ssh/authorized_keys file. The following steps will guide you through this process:
-
Log on to HPCC gateway
gateway.hpcc.msu.eduor start an interactive ondemand session to edit within a linux GUI environment -
On the HPCC, make sure you have a directory named
.sshunder your home directory. If not, create one by runningmkdir ~/.sshin the terminal -
Upload your public key
id_rsa.pubfrom your computer togateway.hpcc.msu.edu. There are multiple ways to do so, as given here. -
Append the public key file to another file
~/.ssh/authorized_keys. In order to do so, assuming that the pub key file has been copied to your home directory from Step 3, you can run the following commandcat ~/id_rsa.pub >> ~/.ssh/authorized_keys -
Set correct permissions by running
chmod 700 ~/.sshchmod 600 ~/.ssh/authorized_keys
Warning
Only copy key files with the .pub extension. Key files without this extension are private keys, which should never be shared!
Via GUI Tools in MobaXTerm
We recommend Windows users use MobaXTerm to generate and manage their key pairs. If you are Windows user who is not comfortable with the command line, the following instructions will guide you through using Graphical User Interface (GUI) tools built into MobaXterm which should work similar to other Windows applications. Please follows these instructions carefully as each step is important to ensure your keys are created using the proper format for use with HPCC.
Generating SSH keypairs using MobaKeyGen
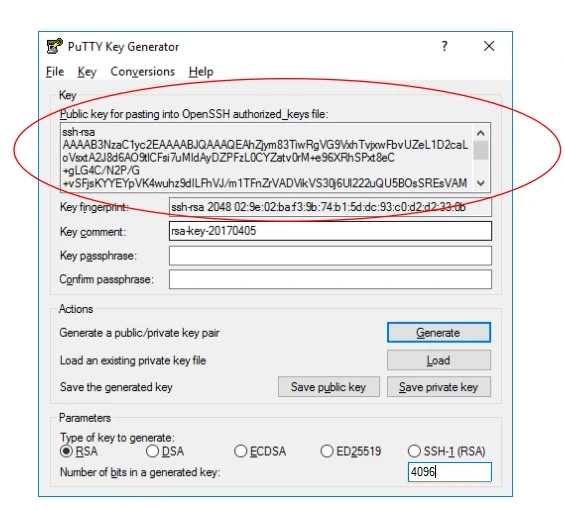
In MobaXTerm, click Tools -> MobaKeyGen (SSH Key Generator) in the menu bar. You will see the following window:
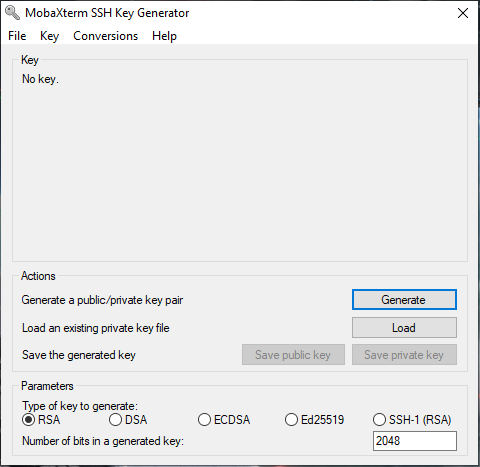
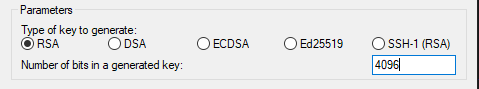
Click Generate and follow the commands on the screen. The Parameters should be set to RSA, Number of bits 4096. The Key comment field can be used to enter a description of the key e.g. "My home PC". As above, we recommend adding a key passphrase.
Save the private key to your computer by going to the Conversions menu at the top of the screen, and selecting "Export OpenSSH key". Save the resulting file in C:\Users\<Account_Name>\.ssh\id_rsa where <Account_Name> is your Windows account name. Create the .ssh directory if it doesn't already exist.
Uploading your public key to the HPCC:
- Copy the Public key from the MobaKeyGen window. Make sure you copy all of the characters.
Note
If you use "Save public key", the file will not be in the correct format.
-
Log on to the HPCC gateway
gateway.hpcc.msu.eduor start an interactive Open OnDemand session -
On the HPCC, make sure you have a directory named
.sshunder your home directory. If not, create one by runningmkdir ~/.sshon the HPCC or using the GUI file browser in the applications menu of an interactive OnDemand session. -
Using an editor on the HPCC, such as
nanoor the editors in the OnDemand GUI session, open or create the~/.ssh/authorized_keysfile and paste the copied public key. Save the file. -
Set correct permissions by running these commands in the HPCC terminal or using the GUI file browser of an OnDemand session
chmod 700 ~/.sshchmod 600 ~/.ssh/authorized_keys
Adding your private key to MobaXterm's SSH connection
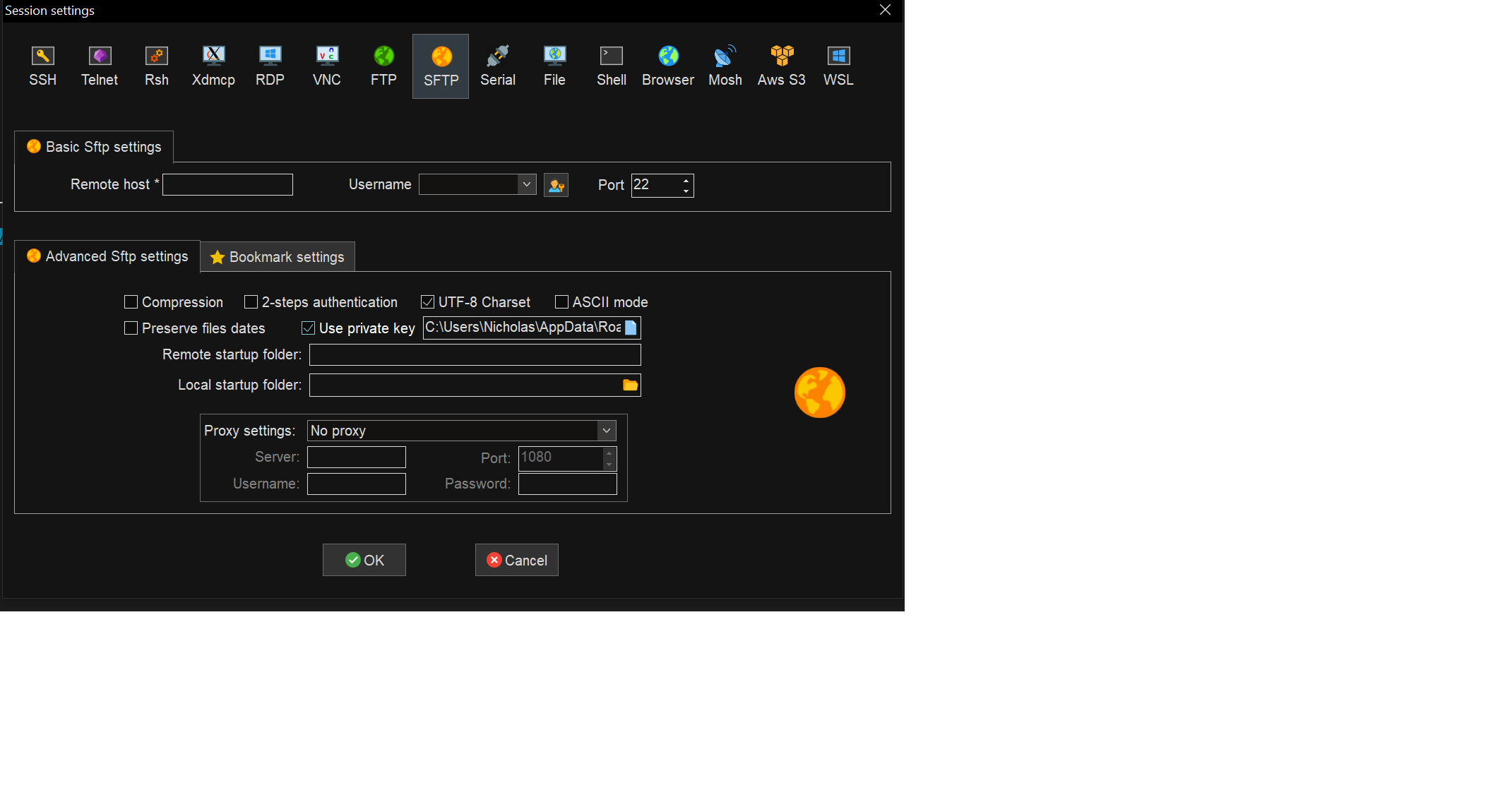
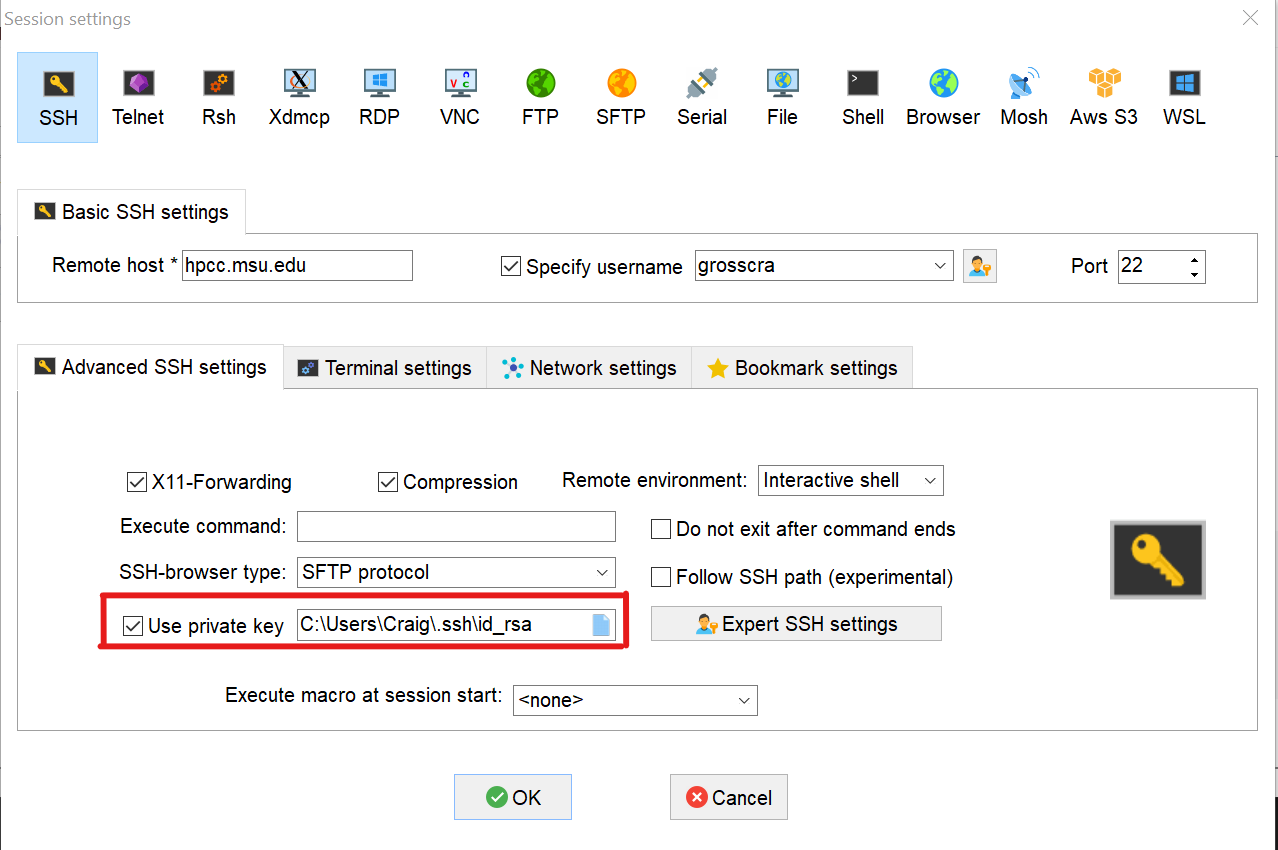
In the MobaXTerm window, in the User sessions pane, right click the link you use to connect to the hpcc (usually something like hpcc.msu.edu (<netid>)), and select "Edit session". In the "Advanced SSH settings" pane, click "Use private key", and add the path to the key file you saved in C:\Users\<Account_Name>\.ssh\id_rsa. Click "OK" to save.
When you use this session in the future, you should no longer be prompted for a password.
Note
If you use MobaXTerm for access, make sure you keep MobaXTerm up to date. We recommend using MobaXTerm to generate keys for use with MobaXTerm on Windows.
Note
If you are having trouble connecting with an SFTP session in MobaXterm to rsync.hpcc.msu.edu, make sure you
check the "Use private key" box and point towards the private key (id_rsa) file which should be in either:
- C:\Users\